
Katalyst Solutions - Web Design & Web Development serving Sterling, VA & Loudoun County & Fairfax County & Northern Virginia

How Can I Protect My Site?
In last week’s post, we discussed the massive WordPress attack and some common reasons why hackers do what they do. As a quick recap on the attack, millions of WordPress sites were attacked using a brute-force password-guessing attack. The hackers targeted the “low hanging fruit” in an attempt to take advantage of website owners who were lax in their approach to security.
Needless to say, no one likes to have their website hacked. It wastes your time restoring your site; you can lose business; and you can endanger other sites and organizations if your site gets used in further attacks.
While there are many sophisticated protections, we’ll focus some of the most basic precautions that can help keep you from becoming the next “low hanging fruit.”
1. Backup, Backup, Backup
Always, always, always backup your system and keep several versions. If you are hacked, those backups may be critical in getting your site up and running again as quickly as possible. It is very possible that you may not realize for weeks or even months that you were hacked. So your best protection then is to have a number of older versions that you can retrieve that can provide a clean base from which to work.
Note: you should also test your backups from time to time to make sure they work. Imagine finding out at a critical moment that all of those backups you have been so careful to make are not working. In the world of technology nothing is a given. So it is better to be safe than sorry.
2. Keep your site patched with the latest security updates
No software is 100% secure. As any software system is developed, security vulnerabilities will be found and software “patches” created to fix those vulnerabilities. Therefore, it is absolutely critical to keep your site up-to-date with the latest security patches. Your out-of-date website is much more likely to be hacked.
The good news is that newer versions of Joomla and WordPress have easy-to-update systems with one-click updates. Just backup the site, run the update, and then test to make sure everything updated and is running properly. Ideally, you should run the updates in a staging or testing area and then move those changes to production once you’ve tested and make sure that everything works.
You should also monitor the extensions you are using on your site. They can have vulnerabilities as well and need to be kept up-to-date.
3. Don’t use “admin” or other common usernames
Logging into a site typically requires two pieces of information: the username and the password. If you use a simple to guess username such as ‘admin’ or your first name, the hacker has 50% of his job done and needs only one more piece of information to accomplish his goal.
Older versions of WordPress don’t allow you to change the default admin username. However, with newer versions of WordPress as well as with Joomla, you can set the administrator’s login name when the site is first installed. You also change it again later. If you still have a username of ‘admin’ on your site, change it to something difficult to guess. I’ll wait here for you until you get back. Got it changed? Good. Let’s keep rolling.
4. Use a secure password
Believe it or not, there are lists of the most commonly used passwords. You would be shocked at the number of people who use passwords like ‘password,’ ‘123456,’ ‘abc123,’ ‘letmein,’ or ‘iloveyou’. Hackers take advantage of these simple-to-guess passwords, because it makes their job really, really easy.
So, what is a secure password?
A ‘secure’ password is one that is really difficult for a computer to guess. For example, your password should be at least 8 characters and preferably 12 or more characters long. It should contain a mixture of upper-case and lower-case letters along with numbers and special characters such as *, !, -, and &. And, you should avoid using your family member’s or pet’s names or other common words that might be found in a dictionary.
Suggestions on Creating and Storing Passwords
One option for creating your passwords is to use a password management application like KeePass (or KeePassX for the Mac). KeePass will store the different passwords for each site or application you use. (Oh, and you are using different usernames and passwords for each site aren’t you?) KeePass also includes a random password generator that will generate – you guessed it - random passwords, which are generally more secure.
Another approach to creating secure passwords is to use memorable phrases such as a favorite saying, a line from a song, or a favorite Bible verse. Take the first letter from each word of the phrase and add some numbers and special characters and you have an easy (or at least easier) password to remember but one that is still more secure.
One last thought on passwords. Don’t write down your password and leave it on a sticky note on your monitor. Sometimes hackers are coming from inside your company. It could be another employee or it could be someone on the janitorial crew coming by your desk at night.
5. Deactivate old users and remove unused extensions
Oftentimes, we’ll see sites where numerous extensions were installed to experiment and test that are no longer in use. These can be prime targets for hackers mainly because website owners will often forget to update the extensions as new versions come out.
Likewise, if you have any users that no longer need to access your site – especially if they have administrative access – it is wise to deactivate their accounts so that those old accounts likewise don’t become targets for hackers.
Conclusion
I hope you’ve gotten a clear picture that any website or computer is a target for hackers. Whether they want to steal credit card numbers, use your system for their own plans of mischief, or just obtain world domination, it is vitally important to take basic security precautions.
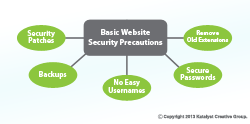
In summary, remember to:
- Backup, backup, backup
- Keep your system up-to-date
- Use a hard-to-guess username
- Use a secure password
- Uninstall / remove unused extensions and inactive users
If you aren’t technically oriented, it is often best to have a maintenance agreement with an outside web development agency with the proper technology skills to keep your system up-to-date and backed up.
The bottom line goal? Don’t be a hacker’s ‘low-hanging fruit!’
Can we help?
Blog
“My expertise is in running my company, not in website design and development. After comparing and contrasting several website development groups, the clear choice became Katalyst Solutions based on overall value, customer service/support, training and the quality of prior websites they developed. I continue to receive support after a successful launch of our website and I enjoy hearing clients compliment our site.”
Tim Reichert, CEO, MBA
Veritax Property Associates
 Click to enlarge
Click to enlarge